We’ve recently been alerted to a recruitment scam that’s using Sourcetoad’s name, logo, and reputation to trick people into fake “remote job” opportunities.
To be absolutely clear:
👉 Sourcetoad only posts legitimate job openings on Indeed and LinkedIn.
👉 We never contact candidates through WhatsApp, Telegram, or unsolicited direct messages.
How We Found Out
Over the past few weeks, several thoughtful people have reached out to us after being contacted by fake recruiters using our name.
-
- A friendly person from Spain reached out to us to say that they had received a WhatsApp message from someone calling themselves “Kai” at +44 7756 218806 offering them a job at Sourcetoad. It felt scammy, so they reached out to us directly.
- A helpful person from Poland emailed us after being invited to a WhatsApp group called “App Innovators Rising to New Horizons,” led by someone calling themselves “Joshua” at +44 7355 863431. They said that it didn’t seem like a real opportunity, so they wanted to confirm with us directly.
- And just recently, another person submitted a detailed report through our website about a LinkedIn user under the name “Gabriel Barbu” who contacted them with a remote job offer. After connecting on WhatsApp, someone using the name “Henry Chan” at the number +44 7563 739019 directed them to a fraudulent domain: aso-sourcetoad.org.
We’re incredibly grateful to these individuals for taking the time to verify and report what they suspected were scams. Their messages helped us connect the dots and act quickly.
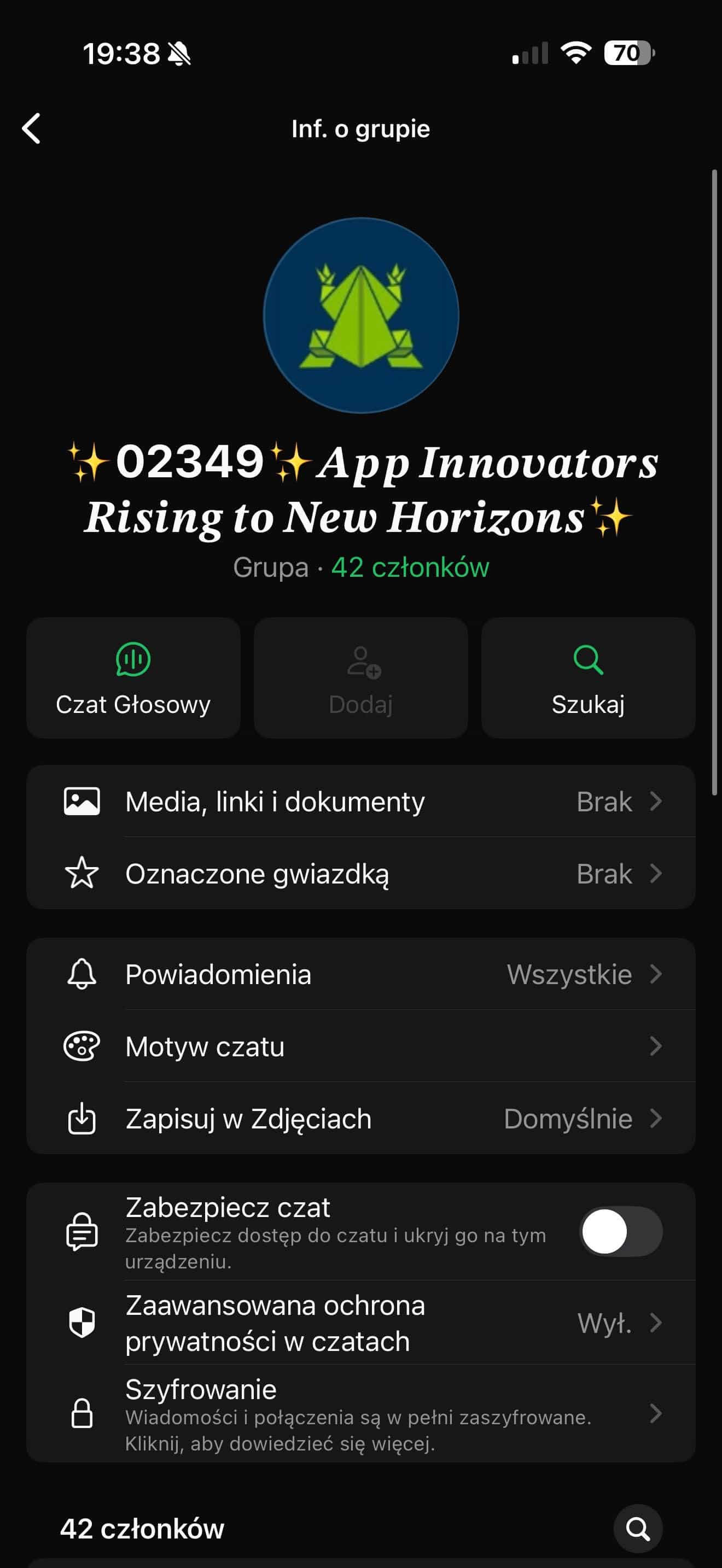
WhatsApp Group impersonating Sourcetoad.
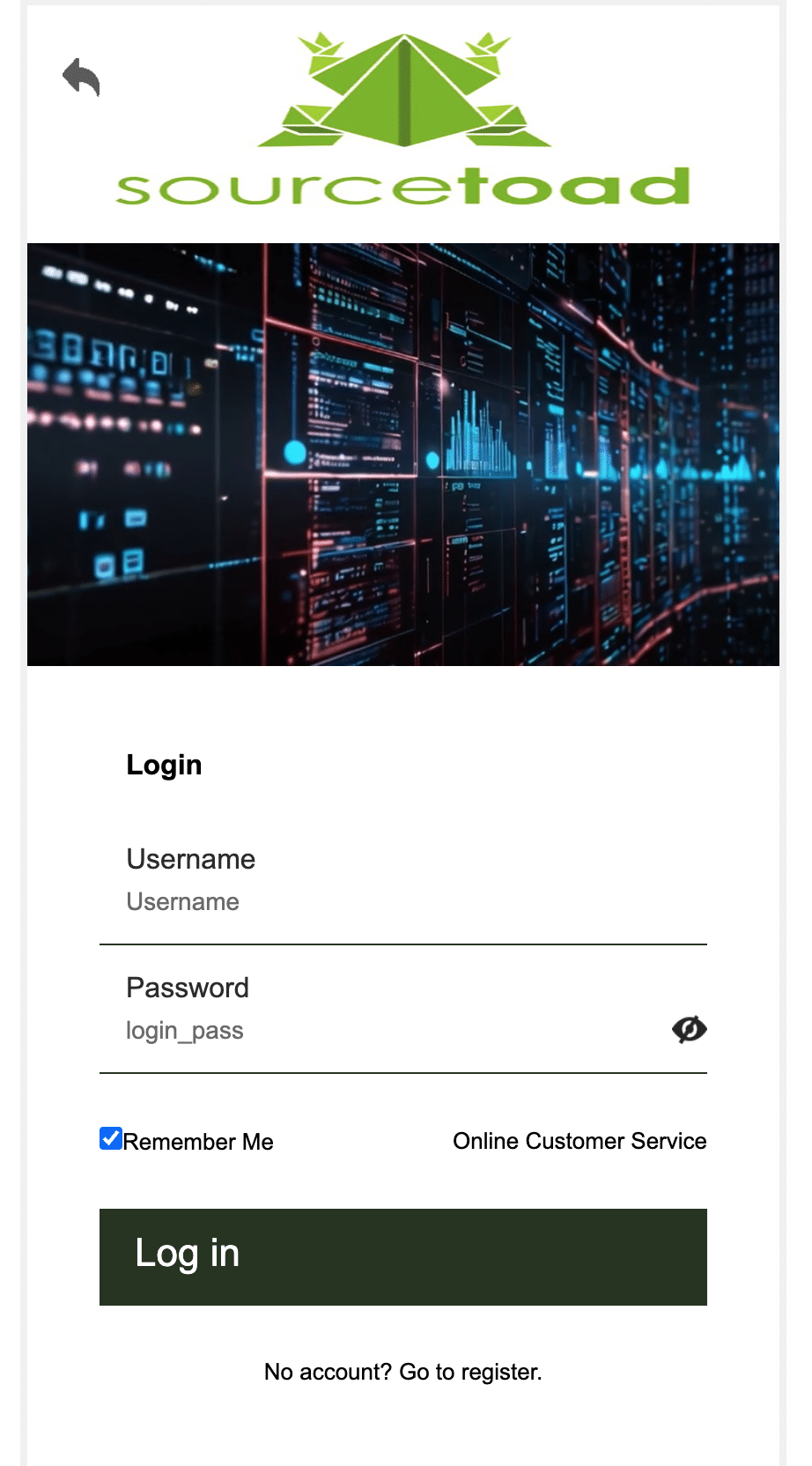
Fraudulent “Sourcetoad” website.
Digging Deeper
We examined the fake site’s source code, domain registration, and related network activity.
The WHOIS records show the domain was registered through Domain International Services Limited (wdomain.com) a registrar that hosts many scam-related domains.
The HTML code we found on the site looked suspiciously familiar: it included mismatched branding from other companies (for example, “Airbnb” labels in hidden modal windows and a “Copyright © 2025 PHD Labs” footer).
When we performed a reverse IP lookup, we discovered several nearly identical websites, only rebranded under different names, one impersonating Airbnb, another copying a UK marketing firm called Brew (who actually does great work helping pubs and restaurants with digital marketing, which sounds awesome!)
All of this confirmed we were looking at a mass-deployed scam network, not a one-off impersonation.
What the Scam Actually Is
These scams follow a clear pattern we’ve now seen multiple times:
-
-
- The Hook: The scammer approaches someone on LinkedIn with a remote job offer, usually something vague but lucrative, like “app optimization” or “AI training.”
- The Setup: They move the conversation to WhatsApp and share a link to a fake “Sourcetoad portal” where the victim is asked to sign up.
- The Illusion: The fake site shows a “dashboard” with made-up earnings for small, simple tasks (clicking buttons, running tests, etc.).
- The Trap: After a few days, the scammers tell the victim they need to make a deposit in crypto (USDC) to “unlock higher-level tasks” or “verify their account.”
- The Loss: Once the money is sent, the scammers disappear or keep asking for more “fees.”
-
In short: it’s a crypto and identity theft scam disguised as a tech job.
How to Handle It (and Help Others)
If your company is ever targeted in a similar way, here’s what we recommend:
1. Collect the Evidence
Gather screenshots, phone numbers, fake domains, and emails. Ask anyone who reports the scam to forward the full message headers or screenshots.
2. Publish a Blog Post Like This
Scammers rely on trust. When you publish a visible warning, victims who search your company name plus “job” or “WhatsApp” will see that you’re legitimate—and that the scam is fake.
3. Contact the Registrar
Use a direct, professional letter to the registrar (in this case, abuse@wdomain.com) explaining that their customer is impersonating your company. Here’s a version of the letter we used:
Subject: Urgent: Fraudulent domain impersonating Sourcetoad — aso-sourcetoad.org
Hello Abuse Team,
The domain aso-sourcetoad.org is being used in a recruitment scam impersonating our company. Victims are directed there through LinkedIn and WhatsApp and asked to “register” for fake jobs and send crypto payments.
Please suspend or disable the domain.
Thank you.
4. Thank the People Who Warned You
The people who report scams aren’t just helping you, they’re preventing others from being defrauded. A simple thank-you goes a long way.
5. Reach Out to Other Victims
If you find other companies being impersonated (like Brew in this case), let them know. Sharing intel helps everyone act faster next time.
Stay Safe
If you’re ever contacted by someone claiming to represent Sourcetoad and offering remote work through WhatsApp, it’s not us. We post all legitimate opportunities only on our LinkedIn page and Indeed profile.
If you’ve received one of these scam messages, please forward it to info@sourcetoad.com so our team can report it.
To everyone who took the time to contact us, thank you. Your vigilance protects others, and it helps legitimate companies like ours keep the internet just a little bit safer.


